
Extreme Networks Control
Software-Driven Session Intelligence for Scalable, Agile Network Visibility

Click here to jump to more pricing!
Overview:
Keep your network edge secure with end-point security
With most data breaches starting at end-points, you need granular control over users and IoT devices and consistent policies across the entire network into multicloud. Our access control solution gives you centralized in-depth visibility and control over all end-point s across your wired and wireless networks through one simple, flexible and easy to consume dashboard.
ExtremeControl securely enables BYOD and Iot to protect your network against external threats. It let s you centrally manage and define granular policies so you can meet compliance obligations, locate, authenticate and apply targeted policies to users and devices.
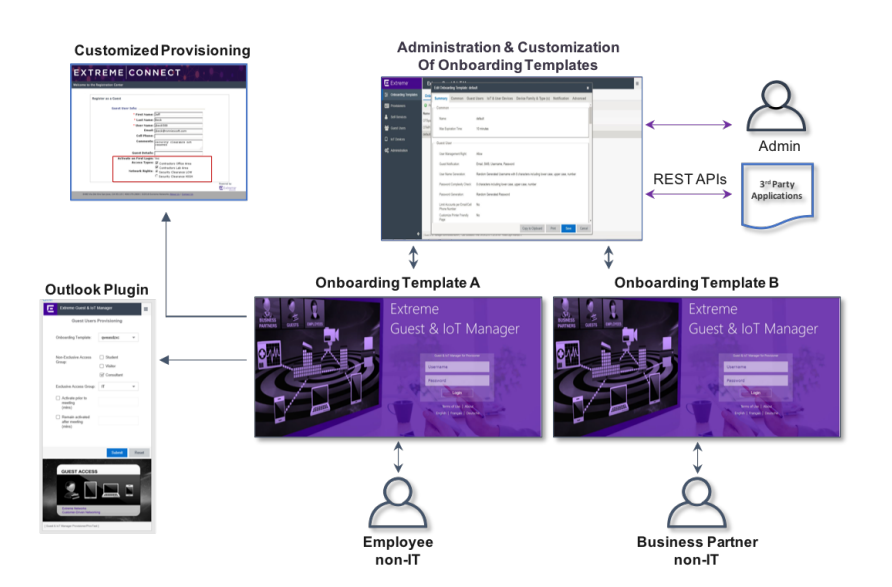
Our identity-aware solution automatically manages expiration, account validit y and time control for guest account s without any IT involvement. Securely and easily onboard guests and BYOD devices with extensive customization, branding and sponsor-based approvals. Built-in device profiling using various internal and external profiling techniques makes sure only devices that comply to your policies can access your network. Users can log into their Yahoo or Salesforce account to complete guest registration.
Secure Your Network with Granular Policy Control and In-Depth Visibility
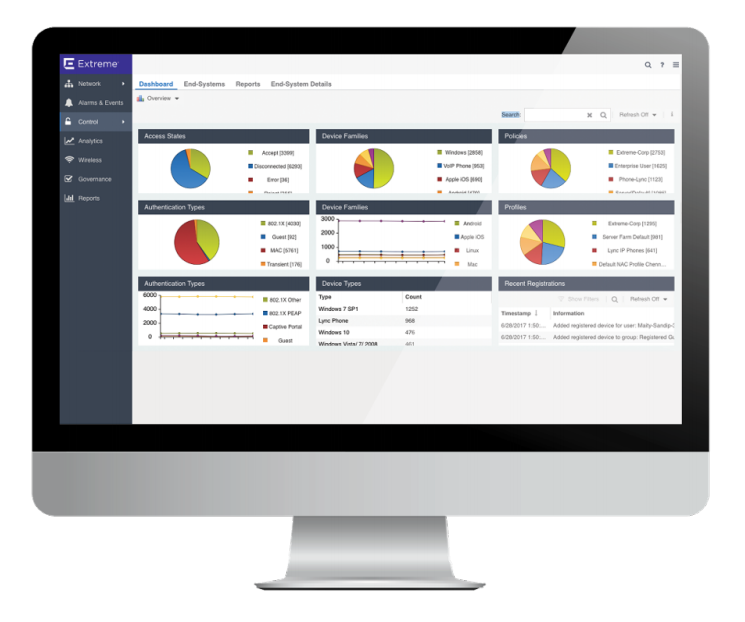
ExremeControl enables you to apply granular controls over who, what, when, where, and how endpoint s are allowed on the network. You can enable secure BYOD, guest access and IoT by rolling out real-time policies based on the securit y posture of devices. ExtremeControl matches endpoint s with attributes, such as user, time, location, vulnerabilit y, or access t ype, to create an all-encompassing contextual identit y. Role based identities follow a user, no matter from where or how she connect s to the network. They can be used to enforce highly secure access policies.
Setting granular policies and scaling them across your network automatically, makes it possible to comply to internal policies and external regulations. With one click you can enforce context-driven policies across devices for QoS, bandwidth and other parameters and align them to your business imperatives. Advanced reporting of all user valid authentications and failures with a real-time state table of all connected users and devices alert s you to potential issues.
Features:
On-Demand Network Visibility

Enable Secure Guests and IoT Access
Customizing onboarding of guests and IoT devices is easy and secure with predefined templates for non-IT personnel

Ensure Consistent Policies Across the Network
Enables consistent policy roll-out across the entire network
Reduce Security Vulnerabilities
Enhances security with agent-based and agentless assessment option
Get Visibility Across Your Network with Advanced Reporting and Alerting
ExtremeControl makes it easy to monitor issues on your network ? all on one simple-to-read dashboard. It sends you advanced, customizable reports and alerts about the authentication, guest access, onboarding, device profiles and authentication, as well as end-system health.
Reduce Security Vulnerabilities with End-System Posture Assessment
ExtremeControl offers both, agent-based and agentless assessment option. We can install either a persistent or dissolvable agent on the client end system or the agent can be downloaded via a captive portal website. It can also be installed via a software distribution system such as Group Policy or System Center Configuration Manager. The agentless assessment does not require an installation or running of any software on the end system.
Expand Security Integrations with Next-Generation Firewalls
Our ExtremeControl is integrated with our ecosystem of partners to expand network security and threat response. Based on alerts from next-generation firewall solutions, we orchestrate endpoint isolation and remediation. We share contextual information such as users, IP address and location for powerful policy enforcement at perimeter firewalls. Policies based on ID-IP mapping follow users.
| Product Part Number | IA-A-25 (87100 ) | IA-A-305 (87101) |
|---|---|---|
| Appliance Specifications | ||
| Storage | 150 GB Enterprise SSD | 240GB Enterprise SSD |
| Networking | 2 x 1GbE | 2 x 1GbE |
| Appliance Scale Number | ||
| Access Control End-Systems | Up to 12,000 | Up to 24,000 |
| Power Specifications | ||
| Redundant Power Supply | 750 W 80 + Platinum Hot Pluggable | 750 W 80 + Platinum Hot Pluggable |
| AC Input Voltage | 90 Hz to 132V and 180V to 264V | 90 Hz to 132V and 180V to 264V |
| AC Input Frequency | 47Hz to 63Hz | 47Hz to 63Hz |
| Physical | ||
| Rackmount/ Dimensions | 1U Rack/ 16.93" x 27.95" x 1.72" | 1U Rack/ 16.93" x 27.95" x 1.72" |
| Weight | 29 lb. (13.15 kg) Max | 29 lb. (13.15 kg) Max |
| Environmental Specifications | ||
| Operating | ASHRAE Class A2 - Continuous Operation. 10 º C to 35º C (50 º F to 95º F) with the maximum rate of change not to exceed 10 °C per hour ASHRAE Class A3 - Includes operation up to 40 C for up to 90 0 hrs per year. ASHRAE Class A4 - Includes operation up to 45C for up to 90 hrs per year. |
ASHRAE Class A2 - Continuous Operation. 10 º C to 35º C (50 º F to 95º F) with the maximum rate of change not to exceed 10 °C per hour ASHRAE Class A3 - Includes operation up to 40 C for up to 90 0 hrs per year. ASHRAE Class A4 - Includes operation up to 45C for up to 90 hrs per year |
| Shipping | -40 º C to 70 º C (-40 º F to 158º F) | -40 º C to 70 º C (-40 º F to 158º F) |
| Humidity (Shipping) | 50 % to 90 %, non-condensing with a maximum wet bulb of 28° C (at temperatures from 25° C to 35° C) | 50 % to 90 %, non-condensing with a maximum wet bulb of 28° C (at temperatures from 25° C to 35° C) |
| Vibration (Unpackaged) | 5 Hz to 50 0 Hz 2.20 g RMS random | 5 Hz to 50 0 Hz 2.20 g RMS random |
Documentation:
Download the ExtremeControl Datasheet (.PDF)

